The Check out is finished just once, so it doesn't initiate each and every time the product boots. The purpose in this article was to write down the 0xF00DBABE frequent to the particular deal with.
Further than holding your cryptocurrencies, it also enables you to communicate with amazing decentralized applications. Want to trade special electronic products or Enjoy game titles without a intermediary? Your Web3 wallet is definitely the go-to tool.
Failed to Feel more details on that considering the fact that a lot of had occurred with each reinstalling Microsoft OS and Ledger Stay App, but... It took a few minutes just before I saw all my copyright, $eighteen,5k bitcoin and about $8k alt coins disappear
This native coin is what you use for paying transaction expenses and taking part in the network, and what community participants acquire in return for retaining that network safe.
Provided the rather anonymous nature of blockchain transactions, it is tough to grasp just but who's the beneficiary of this sum of cash.
Past the description that was copied term for term almost solely through the reputable application inside the Apple Retail store, the application experienced only one five-star score when it was taken and the fraudster employed “Formal Dev” to the developer name.
In addition to the Realst malware, Cado states the "Meeten" Ledger Internet sites host JavaScript that attempts to drain wallets that hook up with the positioning.
" He skipped this obstacle but advised the audience that he was able to attach with a hardware debugger to acquire free access to the chip, which could let reflashing the part with destructive code.
If you receive postal mail regarding your Ledger device, will not act upon it or go to any internet site mentioned while in the letter. As an alternative, contact Ledger assistance to substantiate When the letter you gained is actually a rip-off.
Starting off in October 2020, Ledger consumers started acquiring faux e-mail about a new info breach from Ledger. The email mentioned that the person was influenced via the breach Which they must set up the most recent Model of Ledger Dwell to secure their belongings that has a new pin.
Now, Ledger warns people that its Ledger Connect Package was compromised to include destructive code and that each one people must stay away from working with copyright for now. This destructive code extra for the library can be a wallet drainer that instantly steals copyright and NFTs from wallets that connect with the app.
Ledger informed BleepingComputer they had described the hacker's wallet addresses and that Tether has frozen stolen USDT.
Ledger has assured consumers the Main hardware (Ledger machine) and the primary application software (Ledger Stay) useful for running copyright belongings haven't been compromised or directly affected by this supply chain attack.
Cybercriminals are focusing on folks Doing the job in Web3 with faux small business meetings employing a fraudulent video clip conferencing platform that infects Home windows and Macs with copyright-stealing malware.
 Barret Oliver Then & Now!
Barret Oliver Then & Now! Michael Jordan Then & Now!
Michael Jordan Then & Now! Earvin Johnson III Then & Now!
Earvin Johnson III Then & Now!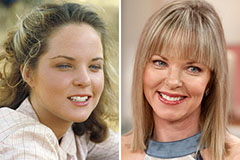 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! Lisa Whelchel Then & Now!
Lisa Whelchel Then & Now!